VNC Behind Firewall: The Ultimate Guide To Secure Remote Access
Ever wondered how you can securely access your computer or server from anywhere, even when it's behind a firewall? VNC behind firewall solutions have become a game-changer for remote work, IT management, and network security. In this article, we'll dive deep into the world of VNC, explore its benefits, and uncover the best practices to ensure your remote connections remain safe and efficient.
Let's face it, remote work is no longer just a trend—it's the norm. But what happens when your network is locked down by a firewall? How do you access your files, applications, and systems without compromising security? That's where VNC comes in. This powerful tool allows you to control your computer remotely, no matter where you are or what obstacles stand in your way.
In this guide, we'll walk you through everything you need to know about VNC behind firewalls. From setting up secure connections to troubleshooting common issues, we've got you covered. So, buckle up and let's get started!
What is VNC Behind Firewall?
First things first, let's break down what VNC behind firewall actually means. VNC, or Virtual Network Computing, is a technology that lets you remotely control another computer as if you were sitting right in front of it. When your target system is protected by a firewall, accessing it remotely can be tricky. Firewalls are designed to block unauthorized access, so getting around them while maintaining security requires some clever strategies.
VNC behind firewall solutions involve configuring your network and VNC settings to allow remote access without exposing your system to potential threats. This can include using port forwarding, proxies, or specialized software that works seamlessly with firewalls.
Why Use VNC Behind Firewall?
There are plenty of reasons why professionals and businesses choose VNC behind firewall setups. Here are some of the most compelling advantages:
- Security: By configuring VNC to work with firewalls, you can ensure that only authorized users gain access to your system.
- Convenience: With VNC, you can access your files, applications, and settings from anywhere, anytime.
- Cost-Effective: VNC eliminates the need for expensive hardware or third-party services, making it an affordable solution for remote work.
- Flexibility: Whether you're managing servers, troubleshooting issues, or collaborating with team members, VNC offers the flexibility you need.
Setting Up VNC Behind Firewall
Now that you understand the basics, let's talk about how to set up VNC behind a firewall. The process may vary depending on your specific network configuration, but here's a general outline to get you started:
Step 1: Configure Your Firewall
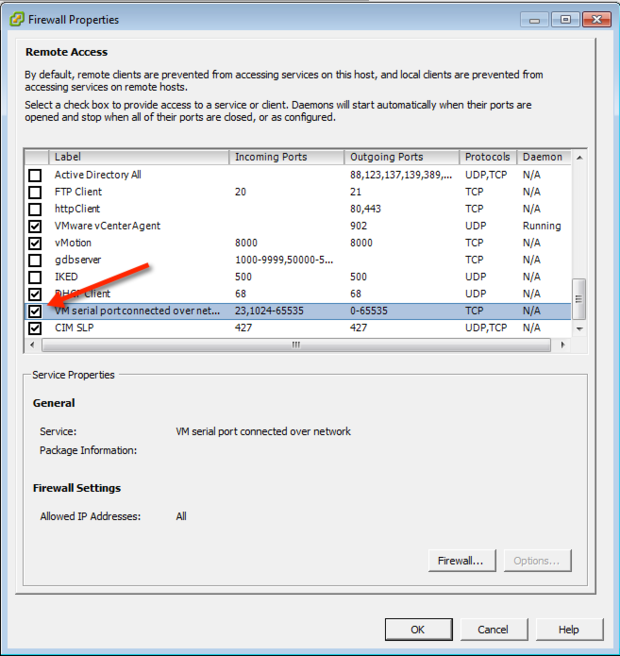
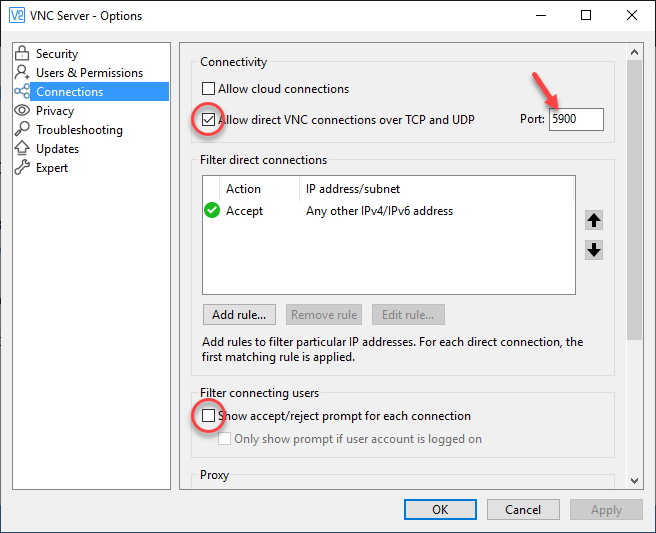
Firewalls are designed to block unauthorized access, so you'll need to configure them to allow VNC traffic. This usually involves opening specific ports (default is 5900 for VNC) and setting up rules to permit incoming connections.
Step 2: Install and Configure VNC Software
There are several VNC clients and servers available, such as TightVNC, RealVNC, and UltraVNC. Choose one that suits your needs and follow the installation instructions. Once installed, configure the software to use the appropriate port and security settings.
Step 3: Test Your Connection
After setting up your firewall and VNC software, it's time to test your connection. Try connecting to your remote system from another device to ensure everything is working as expected. If you encounter any issues, check your firewall settings and VNC configuration for errors.
Best Practices for Secure VNC Connections
Security should always be a top priority when setting up VNC behind a firewall. Here are some best practices to keep your connections safe:
- Use Strong Passwords: Ensure that your VNC passwords are complex and unique to prevent unauthorized access.
- Enable Encryption: Most VNC software offers encryption options to protect your data during transmission. Make sure to enable this feature.
- Limit Access: Restrict VNC access to only those who need it, and consider using IP whitelisting to further enhance security.
- Regularly Update Software: Keep your VNC software and firewall up to date to protect against vulnerabilities and exploits.
Common Issues and Troubleshooting
Even with careful planning, you may encounter issues when setting up VNC behind a firewall. Here are some common problems and how to fix them:
Issue 1: Connection Refused
Solution: Double-check your firewall settings to ensure the correct ports are open and that rules are properly configured. Also, verify that your VNC server is running and listening on the specified port.
Issue 2: Slow Performance
Solution: Optimize your VNC settings by adjusting the color depth and compression levels. Additionally, consider upgrading your internet connection or using a faster VNC client.
Issue 3: Security Concerns
Solution: Implement the best practices mentioned earlier, such as using strong passwords, enabling encryption, and limiting access. You may also want to consider using a Virtual Private Network (VPN) for an extra layer of security.
Advanced Techniques for VNC Behind Firewall
For those looking to take their VNC setup to the next level, here are some advanced techniques to consider:
Using SSH Tunnels
SSH tunneling is a secure way to access your VNC server behind a firewall. By creating an encrypted tunnel between your local machine and the remote system, you can bypass firewall restrictions while maintaining security.
Implementing NAT Traversal
Network Address Translation (NAT) traversal allows you to establish connections between devices on different networks. This can be particularly useful when working with VNC behind firewalls.
Real-World Applications of VNC Behind Firewall
VNC behind firewall solutions have a wide range of applications across various industries. Here are a few examples:
- IT Management: IT professionals use VNC to remotely manage servers, troubleshoot issues, and perform maintenance tasks.
- Remote Work: Employees can access their office computers from home, ensuring productivity and collaboration.
- Education: Teachers and students can use VNC for remote learning, allowing them to share screens and collaborate in real-time.
Data and Statistics on VNC Usage
According to recent studies, the global VNC market is expected to grow significantly in the coming years, driven by the increasing demand for remote work solutions. In fact, a survey conducted by RealVNC found that over 60% of businesses use VNC for remote access and support.
These statistics highlight the growing importance of VNC behind firewall solutions in today's digital landscape. As more organizations adopt remote work policies, the need for secure and efficient remote access tools will only continue to rise.
Future Trends in VNC Technology
The future of VNC behind firewall technology looks promising, with advancements in areas such as:
Enhanced Security Features
As cyber threats become more sophisticated, VNC developers are focusing on improving security features, such as stronger encryption protocols and multi-factor authentication.
Cloud-Based Solutions
Cloud-based VNC services are gaining popularity due to their scalability and ease of use. These solutions allow users to access remote systems without the need for complex configurations or hardware investments.
Conclusion
In conclusion, VNC behind firewall solutions offer a powerful and secure way to access remote systems, making them an essential tool for modern businesses and professionals. By following the best practices outlined in this guide, you can ensure that your VNC setup remains safe and efficient.
We encourage you to share your thoughts and experiences with VNC behind firewall in the comments below. Additionally, don't forget to check out our other articles for more tips and insights on remote work and network security.
Table of Contents
- VNC Behind Firewall: The Ultimate Guide to Secure Remote Access
- What is VNC Behind Firewall?
- Why Use VNC Behind Firewall?
- Setting Up VNC Behind Firewall
- Step 1: Configure Your Firewall
- Step 2: Install and Configure VNC Software
- Step 3: Test Your Connection
- Best Practices for Secure VNC Connections
- Common Issues and Troubleshooting
- Issue 1: Connection Refused
- Issue 2: Slow Performance
- Issue 3: Security Concerns
- Advanced Techniques for VNC Behind Firewall
- Using SSH Tunnels
- Implementing NAT Traversal
- Real-World Applications of VNC Behind Firewall
- Data and Statistics on VNC Usage
- Future Trends in VNC Technology
- Enhanced Security Features
- Cloud-Based Solutions
- Conclusion